The Zero Day vulnerability
The Zero Day threat is probably one of the biggest cyber security problems any small or medium sized organisation that is doing its own IT and security has to deal with. You rely on your anti-virus to snag any incoming threat to your organisation, but there is a gap between the hackers knowing about a vulnerability in your systems and the anti-virus and software vendors discovering the vulnerability for themselves. Only then can they update their software and subsequently your software and protection. This is what is known as the Zero Day threat.
Now there is research that shows the cyber criminals are reacting to zero day vulnerabilities quicker than ever – sending their attacks out into the wild – whilst the software vendors are playing catch-up.
Sometimes vendors get a head start when they or a white hat hacker discover the vulnerability first. But there is always a gap in your defences.
You need to close this gap!
More than just anti-virus and automatic updates
We obviously use well respected anti-virus products, which we constantly review and trust. But today’s business practices, particularly the extensive use of cloud systems and the constantly evolving threat landscape demand more that just anti-virus software. That’s why our smart customers spend the extra and take our advanced threat protection to complement their anti-virus solution.
Industry experts such as Bruce Schneier are now writing about how patches are not the long term solution to our cybersecurity (Schneier, 2018), but patches and updates are what we have now, so let’s do the best we can with them.
Remote monitoring and management (RMM) will alert you if a system you are responsible for has an issue with a patch or an update. The software can also force updates through to staff who refuse to reboot their computer to install an update – this can be a very serious hole in any cybersecurity scheme. However it is better to buy this as a service which includes expert monitoring of and responses to messages when they pose a security or privacy risk to your organisation.
One extra benefit of our RMM is its flexibility – custom monitors for a wide range of software can be installed – and if they do not exist they can be written for you – and it can monitor other operations of the system it is installed on and even wipe it in the case of loss or theft. It can also address the insider threat of a disgruntled or departing member of staff inserting a USB drive into the computer and stealing your customer database.
Create a business model
Understanding quickly whether a specific threat will impact your systems is important. One of the first steps we undertake for both our IT support and cyber security clients is to create a model of the organisation’s systems. We follow the internationally accepted model that is taught at Edinburgh Napier University, among many others, and aids in managing the this risk to your organisation (Whitman and Mattord, 2013)
Training
The last thing I am going to talk about today for closing that cybersecurity risk is training. If you and your people are familiar with social engineering and email phishing techniques the cyber criminals use then the recognition of when such an attack comes is easier.
Below are two of our cybersecurity courses that will equip you and your people with the tools to help plug that cybersecurity gap.
The following course is designed to help a small business owner take positive action over their own cyber security or equip someone from a larger organisation that needs to understand what they need to buy in or what they have already bought – and check it is coming up to standard.
The best source of cybersecurity news
Sorry there was one more thing. Getting the best information you can, so you can respond quickly .
Every day I write a cybersecurity blog, – Smart Thinking Solutions, including urgent posts at weekends – the blog is also summarized here every Friday. In it I highlight those issues across the media that I consider impact the cybersecurity and privacy of businesses and organisations. At Octagon we use it to keep our IT support team up to date and we circulate it to clients to keep them informed. I started writing it just after I graduated and the readership is growing steadily.
You can have the cybersecurity news delivered to your Outlook mail box – not by email – but by RSS feed – a bit of an old technology but I have been in IT a long time. Using this method the emails will not interfere with your business email processing – and you can take a moment to check the cyber- news say with your morning coffee and afternoon tea!
Here is the feed address:
https://smartthinking.solutions/feed
…and here is how to subscribe to the feed in Outlook (from Microsoft):
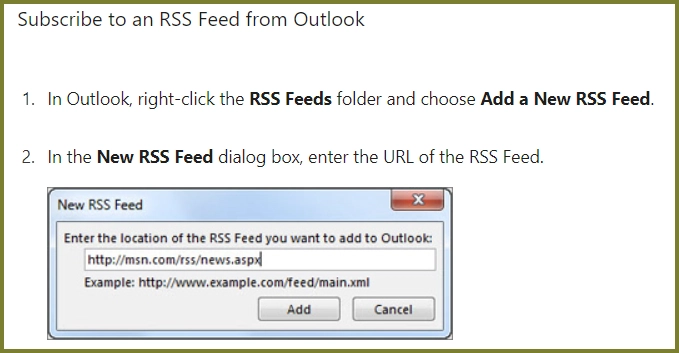
Even easier there is an app for that (here is the iOS one I use but I am sure their are free Android apps as well – just ask Martin):
There it is – why not join a course to build on your knowledge or organise a call with me on Teams to discuss your situation or needs. I am always happy to give a 30 minute online call to anyone who needs some advice – no sales pitch included.
Clive Catton MSc (Cyber Security) – by-line and other articles
References and Further Reading
Zero-day Threat in computing – Wikipedia
White hat (computer security) – Wikipedia
Remote monitoring and management – Wikipedia
Schneier, B. (2018). Click here to kill everybody: Security and survival in a hyper-connected world. WW Norton & Company.
Whitman, M. E., & Mattord, H. J. (2013). Management of information security. Cengage Learning.


