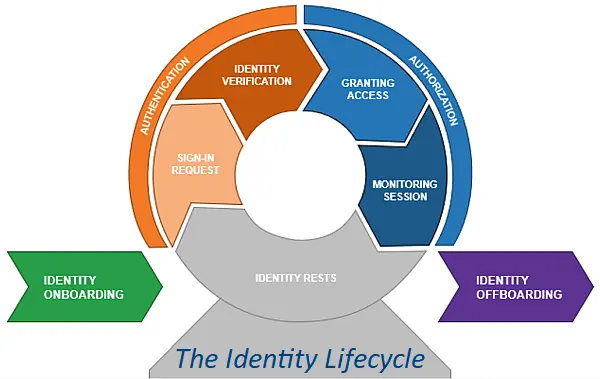
Authentication, Authorisation and Accountability. This is the third part of a three-part series looking at the basics of the cyber security principle of “AAA”.
Day Three – Accountability
Accountability is probably the least enforced part of our Triple A principle in most organisations. But if you do embrace it, it can have a powerful impact on your cyber security.
The Insider Threat and Accountability
Trying to defend against a trusted person inside your organisation abusing that trust is one of the most difficult things in cyber security. (I have a couple of links below to articles covering this issue.) Accountability cannot stop the insider threat but it is a deterrent to casual data theft and abuse to most people you employ.
When sharing is not good
In my first article on authentication I said I would discuss sharing login credentials later – well here it is. For accountability to work people should not share login credentials. Everyone needs their own set and no one should login with someone else’s credentials. It is obvious that accountability breaks down if you cannot be sure of the identity of the user.
One account to rule over all accounts.
Special attention should be paid to any master or global administrator accounts. MFA and logging is obvious but if possible you should set up an alert to indicate when these highly sensitive accounts are being used, giving you real time accountability. If your systems do not offer this, we can issue those alerts for you by importing the system logs directly into our 24/7 continuous monitoring software.
Accountability Everywhere
As with authorisation, it does not just apply to Microsoft 365 and your accounts packages – the principle should be applied to all your systems, where an operational record of use would be a benefit in improving your (cyber) security. Next time that salesperson it trying to sell you this gizmo or that software ask them about the in use logging features and see what they say.
The Cyber Security Investigation – the consequences of a breach.
This is where accountability makes a real difference. I have worked on investigations with logs and without logs and it is obvious that the ones with accountability enforced and a comprehensive set of logs covering many resources always worked out better. Having log-in information, software log, email records and even door entry and CCTV images means the best timeline of an incident can be created.
Remember this is not always done to blame someone but it always done to deal with and then fix an incident.
Authentication, Authorisation and Accountability – a Conclusion
I had a lot more to say on Authentication, Authorisation and Accountability but I had a target of only three easily readable articles to get the basic principles over to you. At university I produced a 5000 word report on AAA, you got about 1000 words!
But I think we got the basics covered.
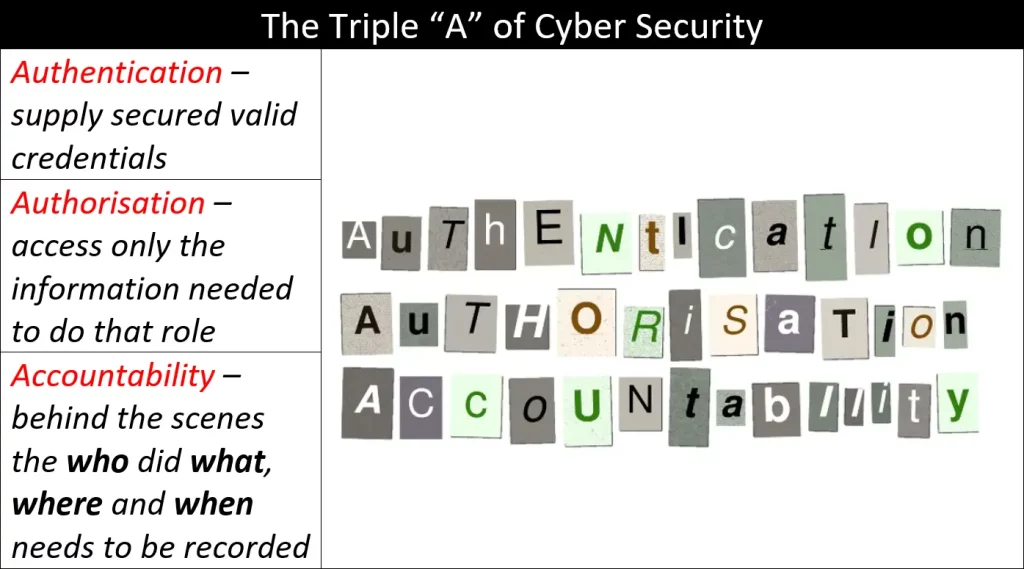
One more thing…
Our soon-to-be-launched expanded 24/7 continuous monitoring and response service will take the logs from across most of these systems, apply both machine learning and threat analysis experts to them and raise an alert if they spot a problem. If it is a game stopper incident, such as active ransomware or an unauthorised user downloading information at 9am on a Monday or 3am on a Saturday, the response team will mitigate the issue.
Is this something you are interested in? Get in touch.
What now?
Ask yourself this question:
“Does your set-up meet these standards?”
Clive Catton MSc (Cyber Security) – by-line and other articles
The Series
Part 1 Authentication – Who Do You Let In?
Part 2 Authorisation – It Shows You Care.
Further Reading
The Insider Threat – the threat landscape and the first steps…
Back again, because that insider threat has not gone away…